In many scenarios, it becomes crucial to control and limit access to your S3 bucket to specific IP addresses. Recently, we encountered a situation where we needed to grant access exclusively to CloudFlare IPs.
To address this requirement, we implemented a solution by incorporating conditions into our S3 bucket policy. This approach allows for fine-grained control over who can access the bucket, providing an added layer of security.
Here’s the policy that proved to be effective for us:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PublicReadGetObject",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::test.nixhive.com/*",
"Condition": {
"IpAddress": {
"aws:SourceIp": [
"173.245.48.0/20",
"103.21.244.0/22",
"103.22.200.0/22",
"103.31.4.0/22",
"141.101.64.0/18",
"108.162.192.0/18",
"190.93.240.0/20",
"188.114.96.0/20",
"197.234.240.0/22",
"198.41.128.0/17",
"162.158.0.0/15",
"104.16.0.0/13",
"104.24.0.0/14",
"172.64.0.0/13",
"131.0.72.0/22"
]
}
}
}
]
}You might need to change the bucket name from test.nixhive.com to your bucketname. The IP given above are belongs to cloudflare. So thee above bucket policy will restrict the traffic from CloudFlare only, making sure your files are not accessed directly via any bot or attacker.
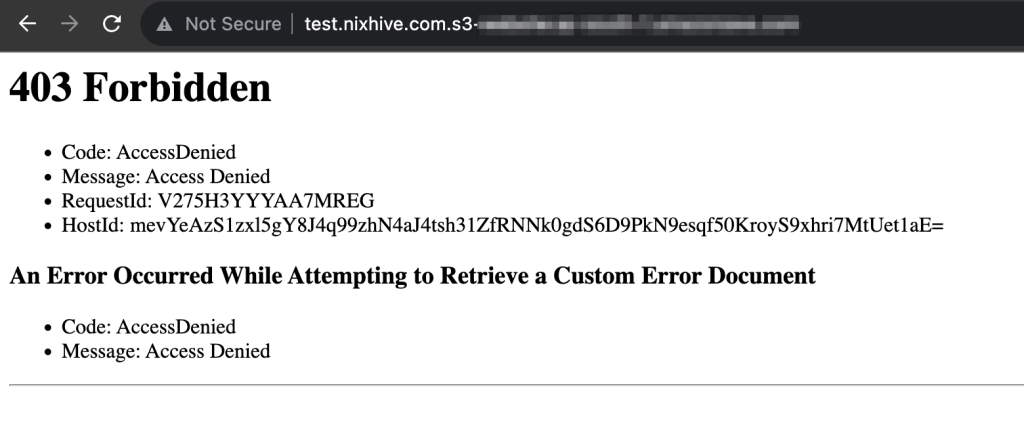
S3 When accessed directly
Accessed via CloudFlare URL