We wanted to give you a heads up about a recent phishing attempt targeting WordPress users. Some of you might have received a deceptive email claiming to be from the WordPress Security Team. This email raises a false alarm about a non-existent vulnerability called “Remote Code Execution (RCE)” on your WordPress website. You might have received this email from tricky domain ending with “@something-wordpress.org”
Here’s the catch: the email urges you to take action by downloading, installing, and activating a plugin supposedly designed to patch the alleged CVE-2024-46188 vulnerability.
But beware! This is a scam, and the mentioned vulnerability doesn’t actually exist. The intention behind this fraudulent email is likely malicious, aiming to compromise your website’s security.
To protect yourself and your WordPress site, avoid falling for this deceptive tactic. Do not download or engage with the suggested plugin.
The Phishing Email looks like this
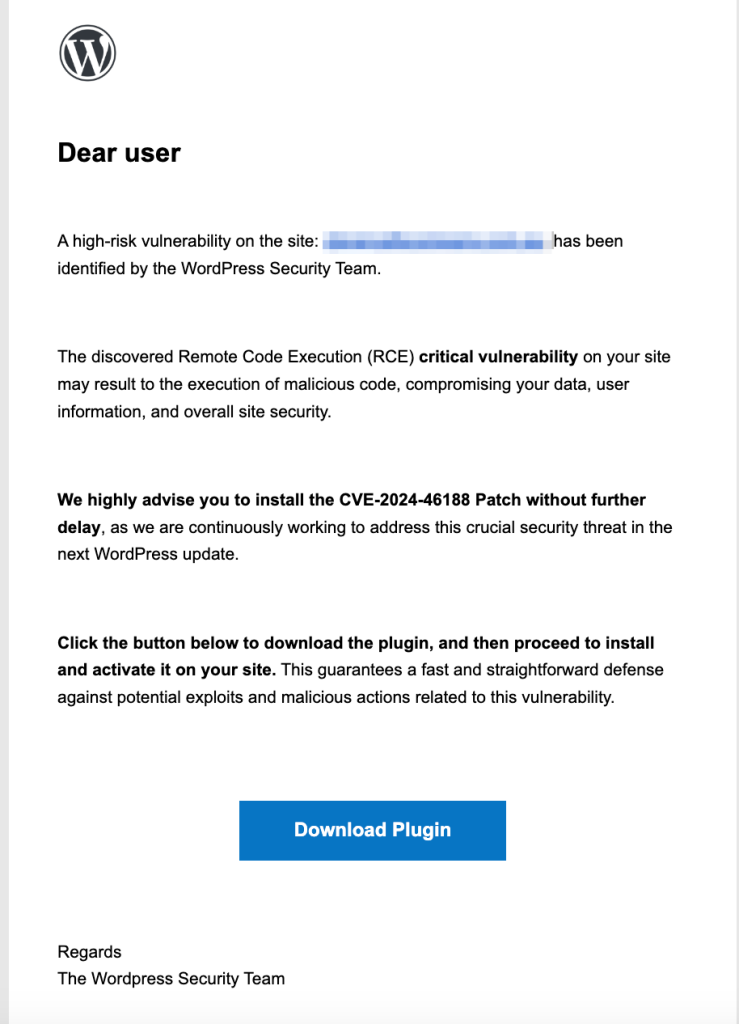
Now lets talk about phishing emails and how to spot them. It’s important to stay vigilant and recognize the signs of a phishing attempt to protect your website and personal information.
- Requests for Plugin or Theme Installation: The WordPress Security Team will never reach out to you via email asking you to install a plugin or theme on your site. Similarly, they will never request your administrator username and password through email. If you receive such requests, it’s a red flag indicating a potential phishing attempt.
- Check the Sender’s Domain: Official emails from the WordPress project will always originate from a @wordpress.org or @wordpress.net domain. Be cautious if you receive emails from unfamiliar domains like “@delivermail-wordpress.org.” Always double-check the sender’s email address to ensure its legitimacy.
- Urgency and Threats: Phishing emails often create a sense of urgency, insisting that you must act immediately to avoid dire consequences. Don’t let panic cloud your judgment. Take a moment to verify the authenticity of the email and its contents before taking any action.
At HAZERCLOUD, we understand the importance of safeguarding your Web Application and Cloud. Our commitment to robust security measures ensures that your experience with us is not just efficient but also secure.
Clean UP – WordPress CVE-2024-46188 Plugin – Services by HAZERCLOUD
If you have accidentally installed CVE-2024-46188 plugin on your WordPress website, please reach out to HAZERCLOUD team immediately to get it cleaned.
Our experienced team specializes in cleaning up after such incidents, ensuring that your website remains secure and free from any malicious elements. Here’s what we can do for you:
- Plugin Removal: We’ll safely remove the deceptive plugin, ensuring it leaves no traces of potential vulnerabilities on your site.
- Security Audit: Our experts will conduct a comprehensive security audit to identify and address any potential security gaps caused by the phishing attempt.
- Password Reset: As an added security measure, we recommend resetting your administrator username and password to prevent unauthorized access.
Don’t let a phishing incident compromise your website’s integrity. Reach out to HAZERCLOUD’s cleanup services, and let us restore your WordPress site.
To get started, simply contact us with the subject “WordPress CVE-2024-46188 Cleanup Assistance,” and our dedicated team will promptly assist you in securing your WordPress environment.
Stay secure, stay confident with HAZERCLOUD!
Source : WordPress News
